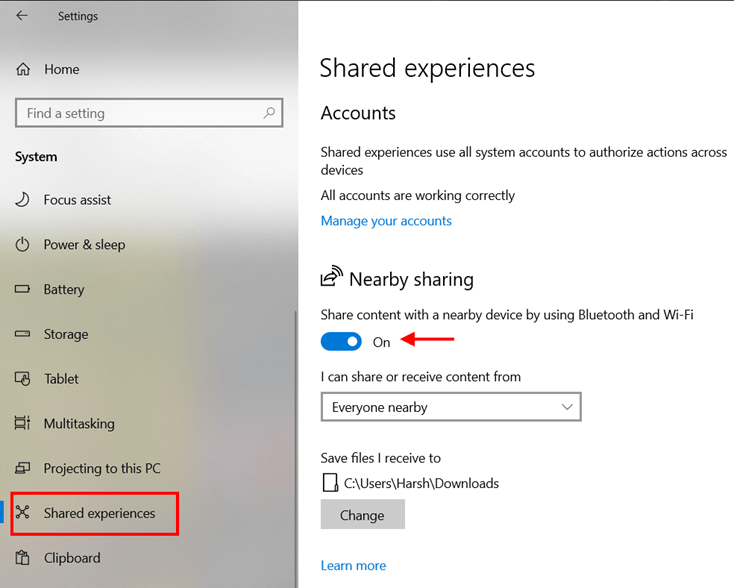
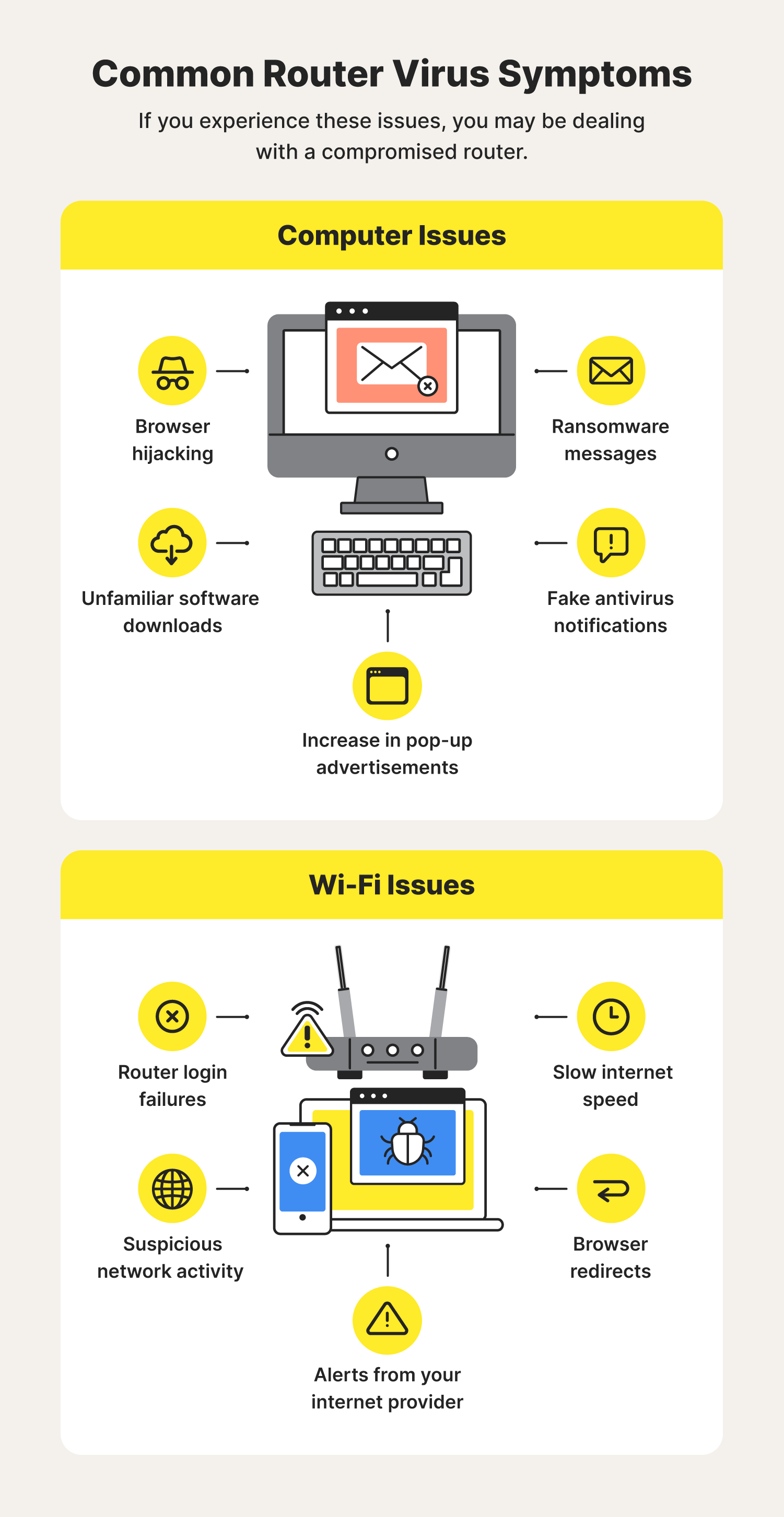
Premium Photo | Internet fraud using computer technology, theft of money on the internet, theft of credit card data. hacker stole a credit card with a fishing rod
Internet and online network security system. Laptop computer hacking, and stealing data from computer laptop Stock Photo - Alamy

Computer Hackers Clipart Transparent PNG Hd, Internet Hacker Stealing Computer Data Illustration, Password, Alarm, Computer Security PNG Image For Free Download

Phishing. A computer hacker who steals money and personal data on the Internet. Web crime with password hacking. The concept of hacker attacks, online fraud and web protection. Vector illustration. 7168224 Vector

Man or hacker stealing data from a laptop at night bending forwards over the keyboard in the glow from the screen as he browses the internet or retrieves and downloads personal data

Hacker Security Steal Your Data and System with Code Internet. Theft of Data from the Computer Stock Vector - Illustration of contemporary, firewall: 74864191

Thief Hacker Stealing Confidential Data Document Folder From Computer Useful For Anti Phishing And Internet Viruses Campaigns Concept Hacking Internet Social Network Stock Illustration - Download Image Now - iStock